Ransomware-Resilient Backups with SyncBackPro
Ransomware is one of the fastest-growing cyber threats in the world. It locks away your data by encrypting files and demands payment to restore them. Even worse, it can attack backup files, leaving you with no clean copy to restore from.
According to Coveware, the average ransomware payment in 2024 exceeded $400,000, and downtime costs often reach millions. The best defense is not paying the ransom, it’s having a ransomware-proof backup strategy.
SyncBackPro makes it possible to protect your data with multiple layers of defense, so you can recover clean copies no matter what.
Core Principles of Ransomware-Resilient Backups
A strong anti-ransomware backup plan should include:
- 3-2-1-1-0 Backup Rule:
- 3 total copies of your data.
- 2 different types of media.
- 1 copy stored offsite.
- Versioned Backups: Keep multiple historical versions of files so encrypted copies don’t overwrite clean ones.
- Offline or Air-Gapped Backups: Backups not continuously connected to the source system, so ransomware can’t reach them.
- Immutable Backups: Backups that can’t be altered or deleted for a set retention period.
Ransomware Detection
SyncBackPro can be configured to detect ransomware infection and stop a backup before it starts. This can avoid your backups from being replaced with infected files. For more details, see our Ransomware Detection with SyncBack article.
How SyncBackPro Protects Against Ransomware
- Versioning and Retention Rules
- Configure profiles to keep multiple versions of every file.
- Example: Retain 10 versions for 30 days to ensure you have a clean restore point even if ransomware lies dormant.
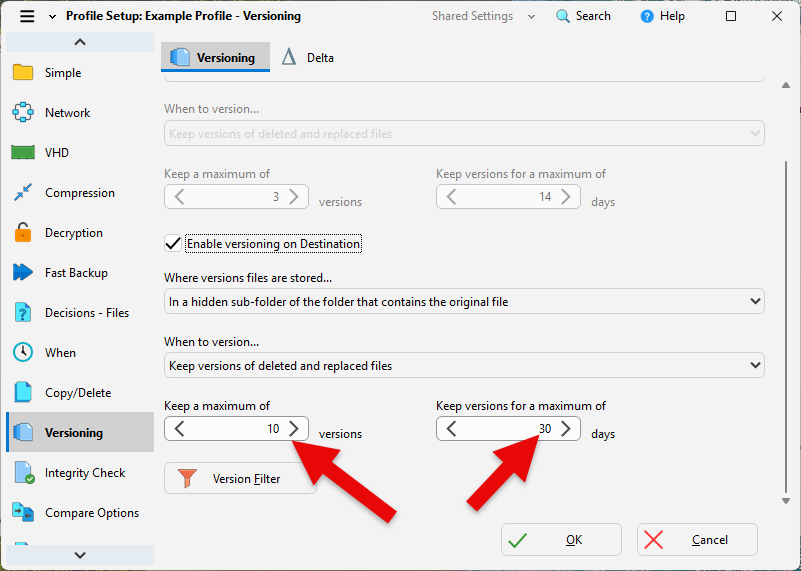
Versioning example: keep 10 versions for 30 days in SyncBackPro. - Immutable Cloud Backups
- SyncBackPro works with cloud providers like Backblaze B2 that enforce immutable storage.
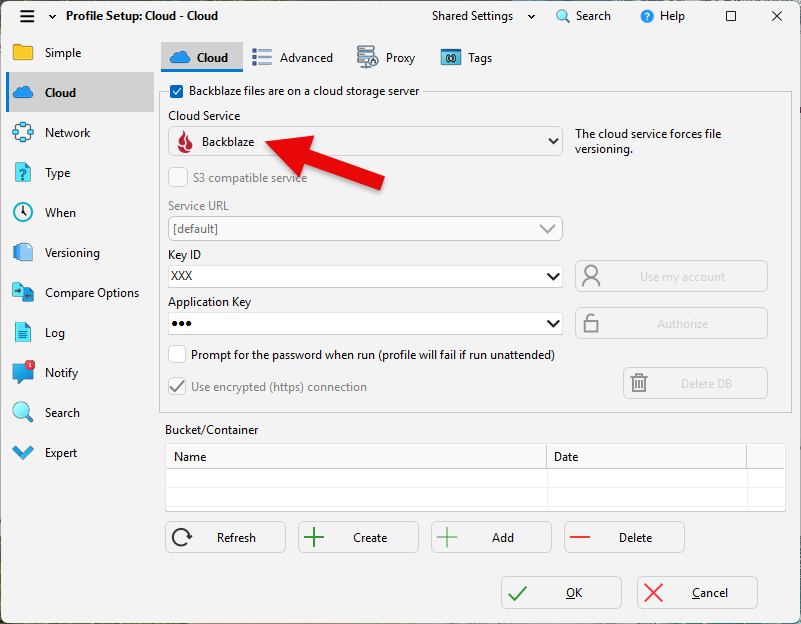
Cloud example: using Backblaze B2 in SyncBackPro. - Offline Backup Rotation
- Schedule backups to external drives or NAS devices.
- Use post-backup scripting to automatically eject USB drives or disconnect network shares after each run.
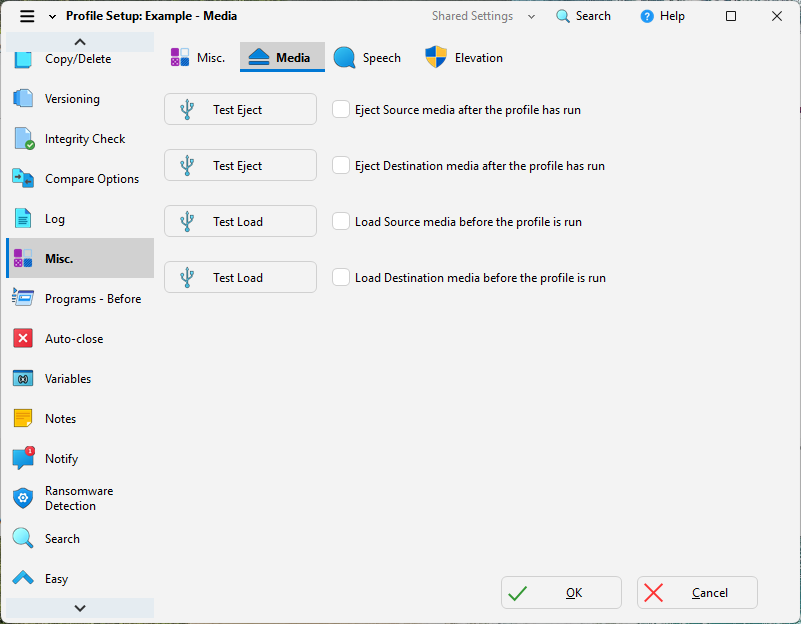
Offline Backup example: ejecting media after SyncBackPro backup profile ends. - Encryption of Backup Data
- SyncBackPro supports AES encryption for both files and profiles.
- If attackers steal your backup files, they can’t open them.
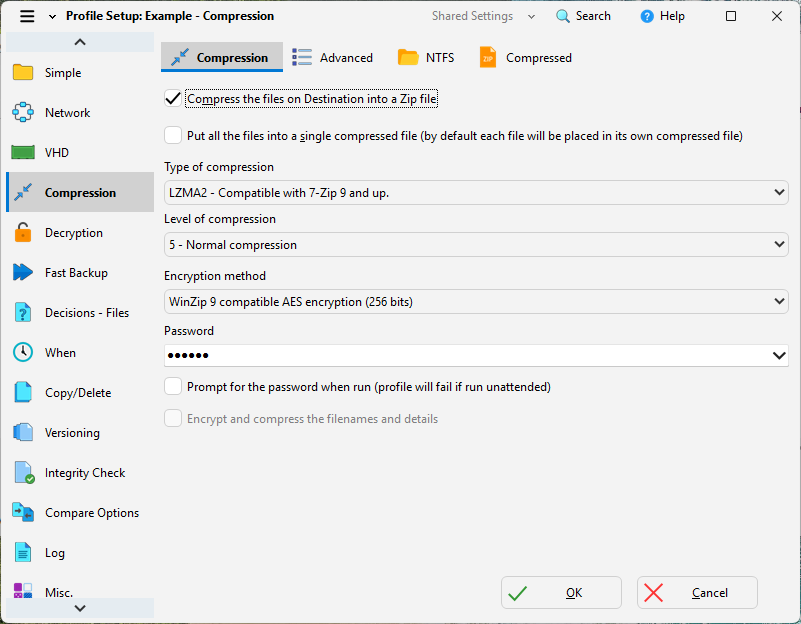
Encryption example: using 256-bit AES encryption in SyncBackPro. - Hash-Based Verification
- Enable hash verification to confirm each backed-up file matches the original.
- This ensures your backup copy is intact before storage.
Verification example: using Copy Verification in SyncBackPro.
Advanced Ransomware Protection Tips
- Disable network shares, or automatically eject media/devices, automatically after backups using SyncBackPro’s scripting options.
- Test your backups regularly: schedule periodic restores to verify clean data recovery.
- Use SBMS (SyncBack Management System) for central policy enforcement across all endpoints.
Example Ransomware-Proof Setup
| Layer | Storage | SyncBackPro Feature | Protection Benefit |
|---|---|---|---|
| Local | External HDD | Versioning + Encryption | Quick recovery, encrypted data |
| Offsite | Backblaze B2 | Cloud feature | Immutable cloud copy |
| Offline | Rotating USB drives | Scheduled backup + auto-eject | Air-gapped, ransomware-proof |
Conclusion
Ransomware can destroy files in seconds, but with SyncBackPro, you can stay one step ahead. By combining versioning, immutable storage, offline rotation, and encryption, you can guarantee safe, recoverable backups, even in the face of a sophisticated attack.
Start your 30-day free trial of SyncBackPro today and build a ransomware-resilient backup plan before you need it.
















