
Advanced Encryption Standards
Author: Swapna Naraharisetty, 2BrightSparks Pte. Ltd.
Encryption methods are used to secure confidential data using mathematical functions known as cryptographic algorithms (ciphers). There are many trusted cryptographic algorithms such as AES, Blowfish and Serpent etc. This article explains in detail about AES encryption and its implementation.
Overview
Advanced Encryption Standard (AES) was invented by Joan Daemen and Vincent Rijmen, and accepted by the US federal government in 2001 and is used worldwide to encrypt sensitive data. It is also referred to as Rijndael, as it is based on the Rijndael algorithm. AES has replaced the Data Encryption Standard (DES) which was published in 1977 to provide high protection against brute force attacks. There are currently no known direct attacks against AES.
General Description of the Algorithm
The algorithm described by AES is a symmetric-key algorithm (the same key is used for both encrypting and decrypting the data) and the design principle is known as a substitution-permutation network (SP-network or SPN) a series of mathematical operations used in cipher algorithms.
This network accepts the plaintext and the key as inputs, and applies several transformation rounds of substitution boxes (S-boxes, it substitutes a block of bits with another block of bits) and permutation boxes (P-boxes, it takes the output of the S-boxes of one round, permutes the bits, and inputs them into the S-boxes of the next round) to produce the cipher-text block.
Decryption is done by simply reversing the process (using the inverses of the S-boxes and P-boxes and applying the round keys in reversed order).
Detailed Description of the Algorithm
AES encryption uses a fixed block size of 128 bits and a key size of 128, 192, or 256 bits. The key size used for an AES cipher specifies the number of cycles of repetition of transformation rounds to use to convert the plain text into cipher text. The number of cycles of repetition are as follows:
- 10 cycles of repetition for 128-bit keys (9 rounds plus one final round)
- 12 cycles of repetition for 192-bit keys (11 rounds plus one final round)
- 14 cycles of repetition for 256-bit keys (13 rounds plus one final round)
Process of AES encryption:
1. KeyExpansions: Using Rijndael's key schedule the initial cipher key is expanded into several separate round keys (known as subkey) for each round of processing.
2. Round: Each regular round involves 4 steps:
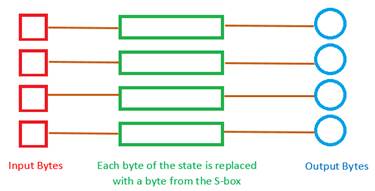
- SubBytes: This is a substitution step where each byte of the state (block of the plain text which is represented as 4×4 matrix) is replaced with another byte from a Substitution box (Rijndael S-box which is derived using mathematical functions)
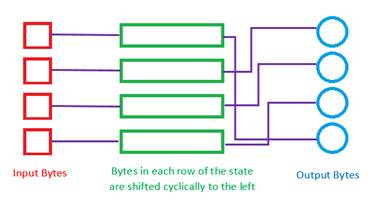
- ShiftRows: This is a transposition step where each byte of a row is shifted cyclically by a certain offset leaving the first row unchanged. Each byte of the second row is shifted to the left by an offset of one, each byte in the third row by an offset of two, and the fourth row by an offset of three. That means Row ‘n’ is shifted left circular by ‘n-1’ bytes.
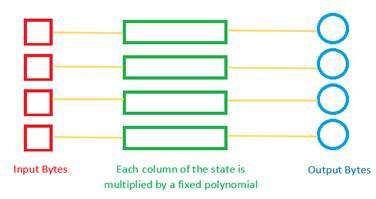
- MixColumns: This is a mixing operation step where the four bytes of each column are combined using an invertible linear transformation (matrix multiplication with a fixed polynomial). The four bytes of the column are taken as input to output four bytes, where each input byte affects all four output bytes.
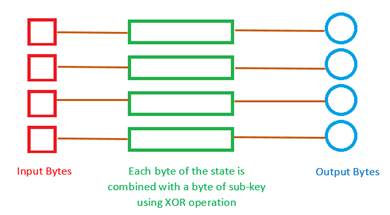
- AddRoundKey: In this step each byte of the state is combined with a corresponding byte of the subkey using bitwise XOR. For each round, a subkey is derived from the main-key using Rijndael’s key schedule and this is combined with the state.
3. Three step Final Round:
- SubBytes
- ShiftRows
- AddRoundKey
Where AES encryption is used in SyncBack
SyncBack Supports AES encryption as it is a secure algorithm, highly efficient and faster in both hardware and software systems.
- AES encryption is one of encryption methods available in SyncBackPro/SE to encrypt the content of the files within a compressed file. SyncBack supports WinZip 9 compatible AES encryption with 128, 192, or 256 bit keys, which can only be decrypted and extracted using newer 3rd party Zip programs, e.g. WinZip 9, 7-Zip etc.,
You can enable AES encryption under:
Modify > Expert > Compression settings page.
Note that Encryption in SyncBack requires Compression to Zip (or equivalent) file. Therefore, to encrypt files you have to first enable Compression.
- AES encryption can also be used to secure the Profile settings in SyncBack. A Profile can contain embedded passwords and sensitive data (for example: passwords for connecting to your NAS drive, Cloud, FTP server, etc.) which by default is encrypted using a simple encryption method, which can be easily decrypted if someone has access to your settings file.
However, you can use 256-bit AES encryption to secure your profile settings and sensitive data. You can enable this option from SyncBack main-interface under:
Global Settings > Encryption tab
This option is available only if your Windows installation allows for 256-bit AES encryption and if you use it to encrypt your Profile settings, then another computer will be able to import the profiles(you export), only if they have the same key file. Although AES encryption is considered as the much stronger method of encryption, it may be possible to decrypt these settings (if someone has access to your settings file), as the key file is stored within SyncBack itself.
Conclusion
The Security, Performance, efficiency and flexibility provided by AES encryption made it an appropriate choice for use in our commercial applications SyncBackPro/SE.
Hence, AES encryption was successfully implemented and supported in SyncBack to encrypt file contents using different keys and varying key sizes. The original data was properly retrieved by decrypting the files using SyncBack or 3rd party Zip programs, e.g. WinZip 9, 7-Zip etc.
Noted Customers
© 2003-2024 2BrightSparks Pte. Ltd. | Home | Support | Privacy | Terms | Affiliate Program


















